Floating Viking Head
Posted on Mon 20 March 2023 in ctf
This is a writeup of the Floating Viking Head challenge which was part of the Reverse category during vikeCTF.
After downloading the attachment we inspect the file with file FloatingVikingHead and see the following output:
FloatingVikingHead: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=5608b8f3df4dfd577212fbc8556e8562e15f4c50, for GNU/Linux 4.4.0, not stripped
Since it is a 64-bit executable we execute it, but of course we don't know the flag yet.
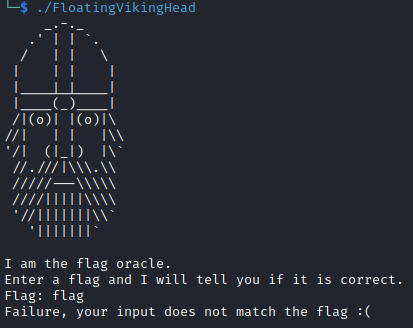
Using strings and running the executable with ltrace and strace resulted in nothing interesting.
Ghirda
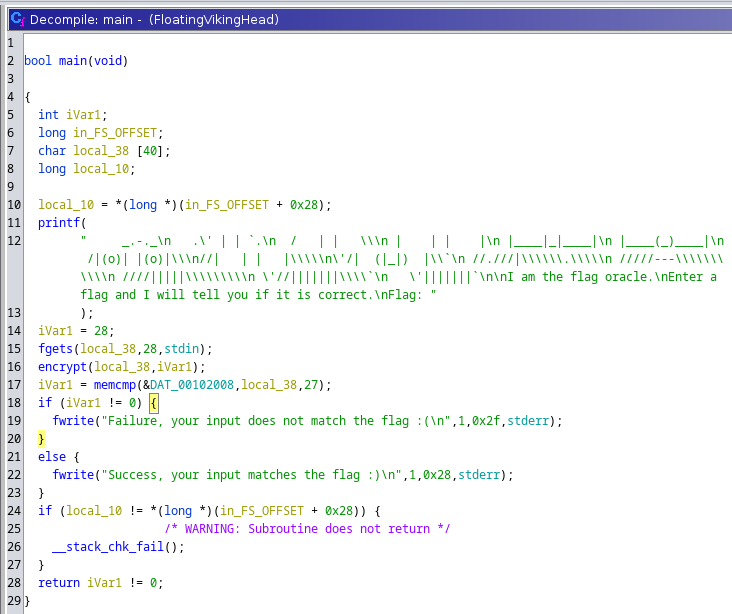
After opening the main function in Ghidra we can see that the executable does the following:
- Read input from stdin
- Call the
encryptfunction to encrypt the input - Compare the bytes at
&DAT_00102008to the encrypted input
So let's see what encypt does:
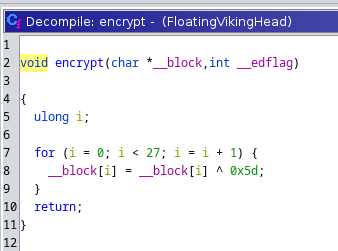
It is just a simple xor.
So we grab data at &DAT_00102008:
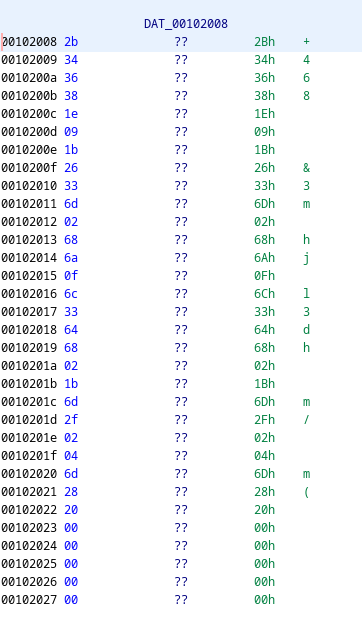
Copying this data as C array we can then decrypt the flag with this simple python script:
for x in [0x2b, 0x34, 0x36, 0x38, 0x1e, 0x09, 0x1b, 0x26, 0x33, 0x6d, 0x02, 0x68, 0x6a, 0x0f, 0x6c, 0x33, 0x64, 0x68, 0x02, 0x1b, 0x6d, 0x2f, 0x02, 0x04, 0x6d, 0x28, 0x20]:
y = x ^ 0x5d
print(chr(y), end='')
Which gives us the flag: vikeCTF{n0_57R1n95_F0r_Y0u}